CSC/ECE 517 Fall 2024 - E2487. Reimplement authorization helper.rb
Background
Problem Statement
Expertiza currently uses session-based authentication in its [AuthorizationHelper] module. The [reimplementation-back-end] however, uses JWT (JSON Web Token) based authentication. This requires a redesign of the AuthorizationHelper module to accommodate JWT-based authentication.
The following points need to be taken care of as per the requirement
- JWT Creation : Make sure that a valid JSON Web Token is created which stores necessary details about the user and their role
- Token expiry and revocation : Token expiry and refresh mechanisms need to be implemented as well as a strategy for token revocation
- Remove dependency on session : The system has to be refactored, configured and tested thoroughly to ensure that having migrated to JWT, there is no dependency on Rails' session
- Writing rspec test cases for all JWT authentication helper methods to ensure proper exception and error handling
Methods to implement
- jwt_verify_and_decode(token): This method will verify and decode a JWT token and return the user's information, including role and claims. Successful verification of the token signature with the secret key will be followed by extraction of the payload which will contain important information about the user and their role for authentication and authorization.
- check_user_privileges(user_info, required_privilege): extract the user's roles or permissions from user_info (e.g., from the decoded JWT payload). Then, check if required_privilege exists within the user's permissions, returning true if it does and false otherwise to control access accordingly.
Further, the already existing methods need to be updated and need to be refactored to account for the new authentication system
JWT Token Overview
A JSON Web Token (JWT) is a compact, URL-safe token format commonly used for securely transmitting information between parties. It is widely used in web applications for authentication and authorization, as it allows information to be verified and trusted. In the context of our reimplemented AuthorizationHelper module, JWT tokens will replace session-based authentication, enabling stateless and more secure access control.
Structure of a JWT A JWT consists of three main parts:
- Header: Contains metadata about the token, such as the type (JWT) and the hashing algorithm used (e.g., HS256 or RS256).
- Payload: Includes claims, which are statements about an entity (typically, the user) and additional data like the user’s role and permissions.
- Signature: A cryptographic signature generated by encoding the header and payload with a secret key or private key, ensuring data integrity.
These three sections are separated by dots (.), forming a token that looks like this: <Header>.<Payload>.<Signature>
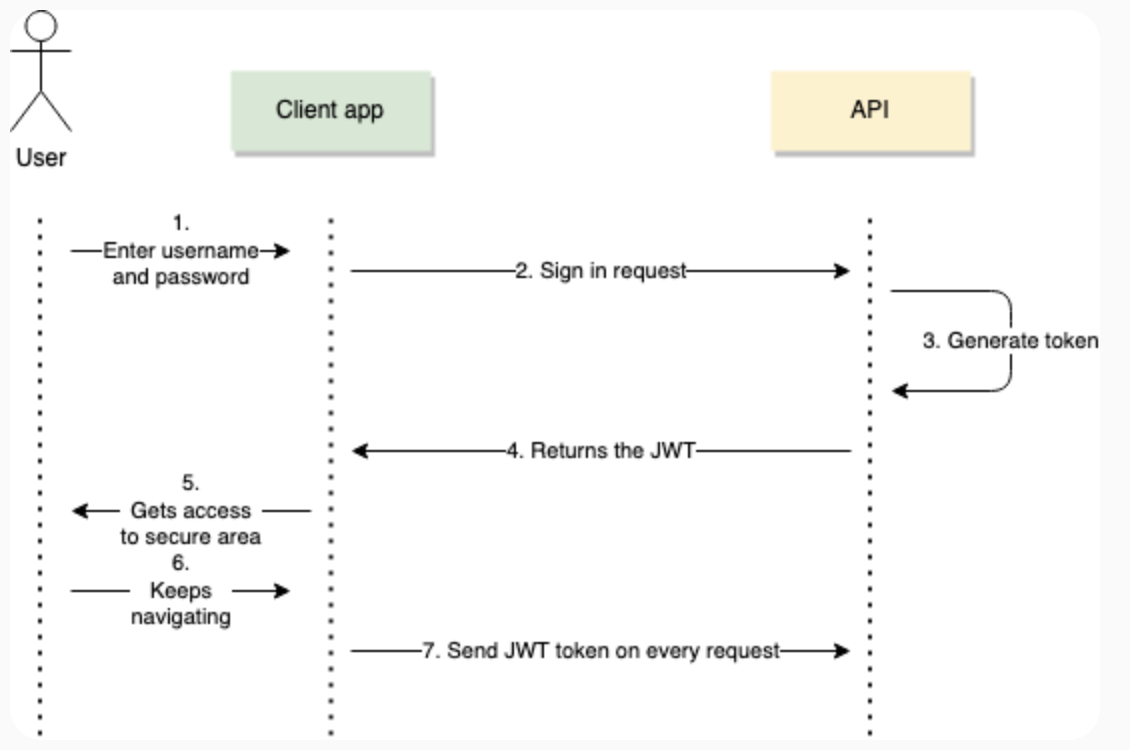
]
Test Plan
Team
Mentor
- Kashika Mallick (kmallick@ncsu.edu)
Members
- Shafa Hassan (shassa22@ncsu.edu)
- Archit Gupta (agupta85@ncsu.edu)
- Ansh Ganatra (aganatr@ncsu.edu)