CSC/ECE 517 Fall 2023 - E2379. Reimplement authorization helper.rb
This wiki page is for the information regarding the changes made for the E2379 OSS assignment for Fall 2023, CSC/ECE 517.
Introduction
Expertiza currently uses session-based authentication in its AuthorizationHelper module. The reimplementation back end uses JSON Web Token (JWT) based authentication. This requires a redesign of the AuthorizationHelper module to accommodate JWT-based authentication.
About Helper
The AuthorizationHelper module provides methods to check a user's privileges and roles within the system. It allows you to determine if the current user has specific roles like Super-Admin, Admin, Instructor, TA, or Student. You can also check if the user is a participant in a particular assignment, instructs an assignment, or has TA mappings for an assignment. Additionally, it provides methods to identify if the current user can perform actions like submitting work, reviewing, or taking quizzes. These functions are essential for managing user permissions and access control in the application.
Requirements
- JWT Authentication Integration: Modify the AuthorizationHelper module to integrate JWT-based authentication, allowing users to authenticate and authorize requests using JWT tokens instead of sessions.
- Token Verification: Implement methods to verify and decode JWT tokens to extract user information and permissions.
- Privilege Verification: Update the existing methods (e.g., current_user_has_super_admin_privileges?, current_user_is_a?, etc) to use JWT claims to determine a user's privileges. Users will be granted access based on their role and claims within the JWT.
- User Identity Verification: Implement a method to verify the identity of the current user based on the JWT token. Ensure that the user's role is validated correctly.
- Methods should be updated to use the user's JWT claims.
- Error Handling: Implement appropriate error handling to deal with JWT verification failures or unauthorized access attempts.
Methods to be implemented
- jwt_verify_and_decode(token): This method will verify and decode a JWT token and return the user's information, including role and claims.
- check_user_privileges(user_info, required_privilege): Given user information from the JWT and a required privilege, this method will determine if the user has the required privilege.
- Update and adapt the existing methods to use JWT claims for authentication and authorization.
Deliverables
- A modified and fully functional AuthorizationHelper module with JWT-based authentication.
- Updated methods to ensure JWT claims are used for authentication and authorization.
- Appropriate error handling to handle JWT-related issues.
- Unit tests should cover different scenarios and edge cases to ensure that each function works as expected
- Comments for every function.
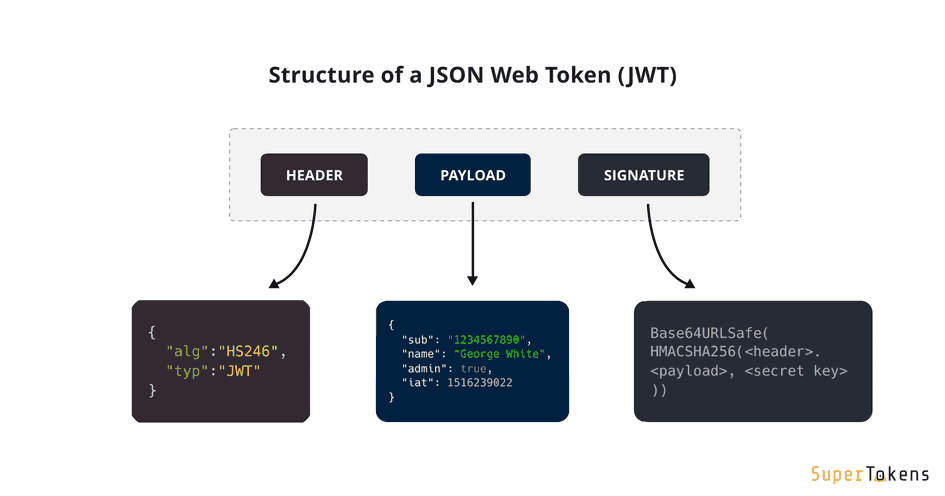
JWT Token
A JWT contains three parts:
- Header: Consists of two parts: The signing algorithm that’s being used and the type of token.
- Payload: The payload contains the claims or the JSON object.
- Signature: A string that is generated via a cryptographic algorithm that can be used to verify the integrity of the JSON payload.
Methods Details
- Error Handling: The method is wrapped in a begin and rescue block to handle JWT::DecodeError. If an error occurs during the decoding process (e.g., an invalid signature or expired token), the method returns nil.
Error Handling
rescue JWT::DecodeError nil end
- check_user_privileges(user_info, required_privilege): The check_user_privileges method is responsible for determining whether a user, based on their role and claims stored in a JSON Web Token (JWT), possesses the required privilege within the context of the application.
Pseudo Code
function check_user_privileges(user_info, required_privilege):
Check if User info is null
return false
switch statement:
case 'Administrator':
return user_info[:role] == 'Administrator' OR user_info[:role] == 'Super-Administrator'
case 'Student':
return user_info[:role] == 'Student' OR user_info[:role] == 'Teaching Assistant' OR user_info[:role] == 'Instructor' OR user_info[:role] == 'Administrator' OR user_info[:role] == 'Super-Administrator'
Other cases
default:
return false
- Updating existing methods in the helper wherever session is being used.
Test Plan
- JWT Authentication Integration
Objectives:
- Verify JWT Token Processing:
Confirm that JWT tokens are correctly processed, verified, and decoded.
- User Privilege Verification:
Ensure that user privileges are correctly verified based on JWT claims.
- User Identity Verification:
Confirm that the user's identity is accurately verified based on the JWT token.
- Existing Methods Update:
Validate that existing methods are successfully updated to use JWT claims.
Test Cases
- JWT Token Processing:
Verify that a valid JWT token is successfully processed and decoded. Test with an invalid token to ensure proper error handling.
- User Privilege Verification:
Check user privileges for various roles (super admin, admin, instructor, TA, student). Verify user privileges for specific actions (submitting work, reviewing, etc.).
- Error Handling:
Test error handling for JWT verification failures. Attempt unauthorized access and validate appropriate error handling.
- User Identity Verification:
Verify the correct identification of the current user based on the JWT token. Test with various roles to ensure accurate identification.
- Existing Methods Update:
Confirm that existing methods are updated to use JWT claims for authentication and authorization. Validate the behavior of updated methods with various scenarios.
Existing methods to be updated
- current_user_has_super_admin_privileges
- current_user_is_a?
Team
Mentor
- Ameya Vaichalikar (agvaicha)
Members
- Sravya Karanam (skarana)
- Sucharitha Nadendla (snadend3)
- Abhishek Desai (adesai7)